 A general impression about security testing that most of the companies have is that it is a process of hacking a website after the developing parts is done and/or the application is launched.
A general impression about security testing that most of the companies have is that it is a process of hacking a website after the developing parts is done and/or the application is launched.
This idea still stands up because the cyber security field was poorly addressed, or even ignored by most of software development companies, even though the danger security risks are always exploited and global actors have been victims of cyber attacks.
In fact, for a company focusing on the security of the applications they build, for their clients or for themselves, the idea that the customer has in mind is the most important. When a website or application works with personal data, online transactions or other confidential information, the user has to trust that application. Before building any piece of functionality, you need to figure oyr first how that functionality will correspond to the security principles.
If we divide the Software Development Life Cycle (SDLC) into five phases: Define, Design, Develop, Deploy and Maintain, security testing should be done starting from the Define phase, which can be also divided into the following phases: Process Reviews & Manual Inspections, Code Review and Security (Penetration) Testing.
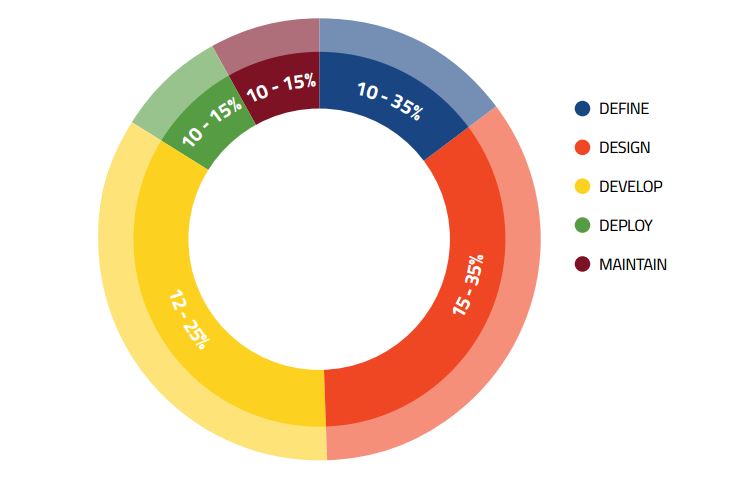
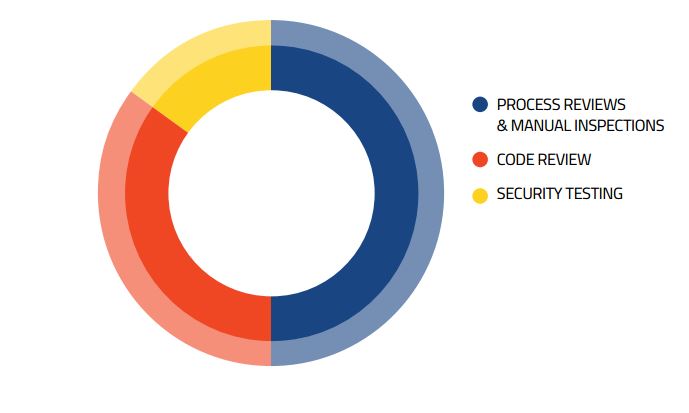
In the above diagrams, it is highlighted the test effort needed in each of the phases over the SDLC and, particularly, in the Define phase.
Define and Design phases focus on the technical and functional architecture, specifications are written down and concluded and those need to be reviewed by security experts, in order to identify areas with high-security importance.
In these two phases, the tester should work with the software architect of the project. The focus will fall on components that might require firewalls, encryption, special authentication or areas with complex authorisation.
The Development phase is the most active one, requiring manually or automate investigations of the code behind the application, especially for the places where the input data is validated or where the business logic constraints are strengthened. Also, testers should check for possible situations in which memory corruption might happen and see how the web application communicates with the OS.
Learning defensive coding could be suggested to developers, in this way they would be directly involved in the security testing phase.
Brute security testing can be done after the application is in final states before launching. Here, there are many options that could be approached. The most common one are:
- black-box testing, to find what an attacker with no knowledge about the system could find out;
- white-box testing, to investigate the impact of the breach from inside attacks.
According to the company’s needs and expectations, other options could be:
- penetration testing, case in which the tester not only finds vulnerabilities, but also tries to exploit them and determine the impact of the breach;
- vulnerability assessment, case in which the challenge is to find all the possible vulnerabilities, without trying to exploit them.
In the Maintenance phase, the software is already launched and the user experience can be analysed. Testers can review access logs and error logs, trying new penetration procedures or, if new patches are added, then a new session of pen-testing may be required.
If we split the security testing phases over the SDLC, it can be seen that there are a lot of actions to be done before what we call the actual security testing.
Currently, most companies that deal with security testing in their development process rely on the security of the framework they use, until the penetration testing (architectural, coding, etc.), which is done at the end of the developing stage, thinking that this is enough. The reality is that this is working only for the standard components of the framework, but when it comes to custom made functionalities, then the skills of the developer might affect the security level of the application.
Also, an important issued found when penetration testing is done only in the final stages (the software is ready to be launched on the market) is that when huge breaches are found, the cost of fixing them is very high, especially because of the development effort needed for fixing them.
To conclude, security testing is a field that stands on its own, which has to be rigorously planned and treated with a lot of interest by experts with experience. To ensure users trust, security testing has to begin with the business value and to go on for the whole life cycle of an application.
Author: Andrei Pusoiu



